Hidden in plain sight: mitigating the dangers of browser extensions (2/2)
FEBRUARY 21, 2020 | FINGERPRINTS
Browsers extensions are a significant risk to any business that depends on managing multiple accounts. In the first part of this two-part series, we explained four areas of browser extension detection. In this second part, we reveal how extension detection is far from theoretical experimentation, but is in fact used by big names like LinkedIn and YouTube.
We then explain further the privacy implications and, crucially, the ways you can mitigate these risks.
How prevalent is extension detection in the wild?
Empirically we can see that extension detection is applied by numerous websites, even by most famous ones. For example, when you visit YouTube.com, the website checks the existence of the Chrome Media Router extension by probing the WAR files of the extension.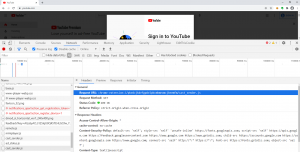 Another example is LinkedIn, one of the most widely used business networks in the world. The site checks 18 extensions that can be used to exfiltrate data from the platform.
Another example is LinkedIn, one of the most widely used business networks in the world. The site checks 18 extensions that can be used to exfiltrate data from the platform.
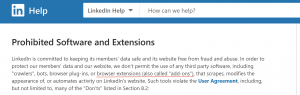
![Add-ons LinkedIn prevents [1]](png/linkedin-extension-detection-2-300x46.png) In the case of finding existence of these extensions, LinkedIn bans or restrict users even though some of these extensions have a legitimate use. [2]
In the case of finding existence of these extensions, LinkedIn bans or restrict users even though some of these extensions have a legitimate use. [2]
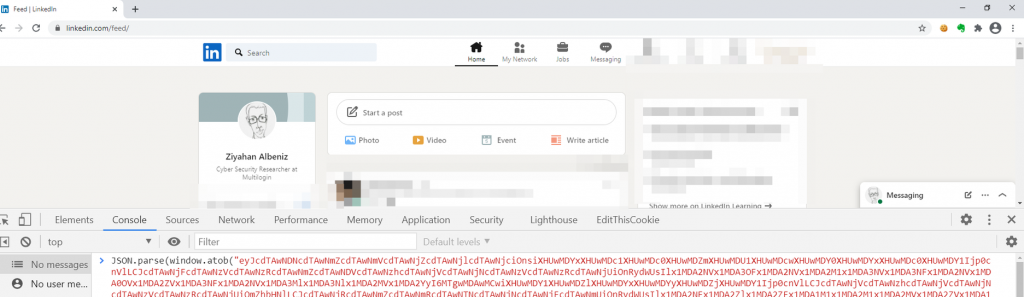 LinkedIn stores extensions that will be checked in localStorage with the name C_C_M. To see details of which extensions are being checked by Linkedin:
LinkedIn stores extensions that will be checked in localStorage with the name C_C_M. To see details of which extensions are being checked by Linkedin:
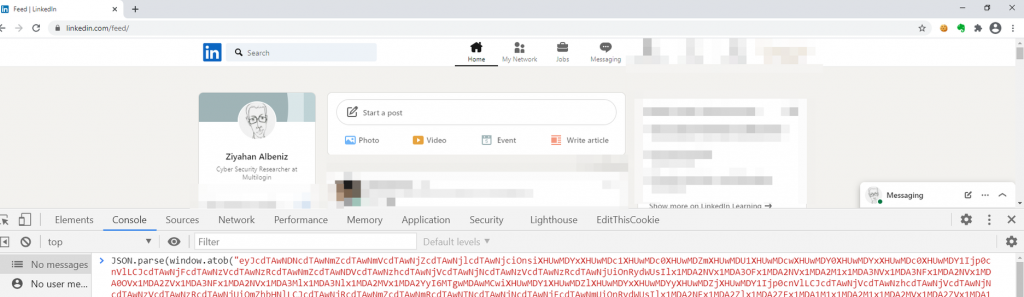
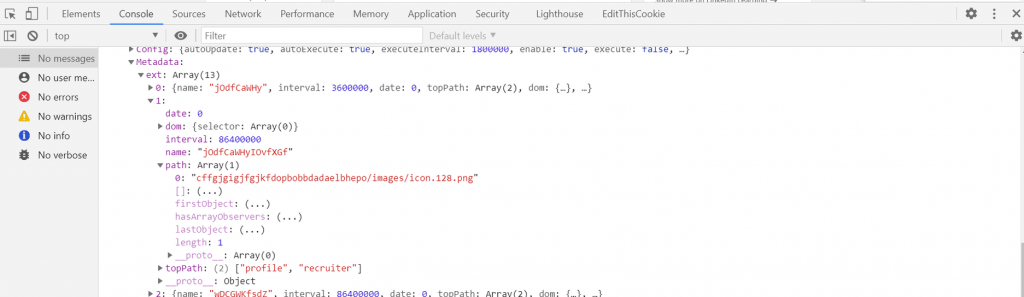 Below are some of the extensions that LinkedIn tries to probe:
Below are some of the extensions that LinkedIn tries to probe:
SalesLoft Connect (cffgjgigjfgjkfdopbobbdadaelbhepo)
Discoverly (dijhcpbkalfgkcebgoncjmfpbamihgaf)
Ebsta for Bullhorn (bneepngbmdnjodaceeffcodionfphgcb)
Ebsta For Salesforce (gemcgnkghpnfbmlfimdbdgfepcgenphf)
One2Lead - LinkedIn Automation Tool (mdbaimghogkgfpkgmjfbkjnjamhkbnmm)
Social Lookup (ppomfpehkfdkogbloajgjllonjlnjdeh)
Entelo (nogdppkjhdnlpkbbdbgpmekmbfpkkogb)
To circle back around to our question of the prevalence of browser extension detection, the figure is around 25% of the Alexa top 10,000 domains. In fact, this is backed up by recent research by Alexander Sjösten, which shows that in 2019, some 2,572 of these domains probe for WAR – which is also a substantial increase compared to just 66 domains doing so in 2017.
25% of the Alexa top 10,000 domains, including LinkedIn and YouTube, use browser extension detection.
What are the privacy implications of extension detection?
There are lots of reasons behind extension detection. For example, websites can use it to understand if an accompanying program is installed on the browser, as we see in the Chromecast extension. The most concerning for many of our readers, however, is as part of browser fingerprinting.
Extension detection as part of browser fingerprinting
Having read this far, it probably won't surprise you to know that anonymity is far from a given with browser extensions – but it should concern you.
To understand the figures, think about the concept of anonymity set size. This essentially describes how many distinct devices share the same browser fingerprint. For example, if the anonymity set size is 1, it means that the browser fingerprint is unique. If the anonymity set size is 5, there are 5 distinct devices with the exact same fingerprint.
A large number of extensions have very few, or even only one unique user – can you imagine what your anonymity set size would be among millions of browser users when you use an extension with a handful of users if this extension is detected through its effects on WAR or DOM? Just look at recent research; Extension Monitor showed that in 2019 "25,540 extensions (13% of the total) have just one user"; likewise, "All in all, about 50% of Chrome extensions have fewer than 16 installs."
Despite the decision in 2015 that all browsers would use the same structure for browser extensions, different browser vendors do deliver extensions through different extension markets. While Google Chrome, uses Google Chrome Store, Firefox delivers extensions on Firefox Browser Add-Ons. Edge prefers to deliver extensions over Microsoft Edge Add-Ons; Opera delivers on Opera Add-Ons, etc.
50% of Chrome extensions have fewer than 16 users
Let’s imagine an actor that wants to understand the brand of the browser you use. This actor decided that you use Grammarly extension by looking at the DOM:
1document.body.hasAttribute("data-gr-ext-installed")
Grammarly is delivered in three browsers on their own extension market: Chrome, Edge and Firefox. The next step is too easy. Just by using each extension ID used by different extension market, this actor can understand which browser you use.
Here is an example of the WAR URL of the Grammarly browser extension:
X-extension://EXTENSION_ID/src/images/eea2fd77fd2e973f20b26f45426b4c2c/[email protected]
Detecting Chrome/Chromium/Vivaldi:
1// Extension ID: kbfnbcaeplbcioakkpcpgfkobkghlhen2<img src="chrome-extension://kbfnbcaeplbcioakkpcpgfkobkghlhen/src/images/eea2fd77fd2e973f20b26f45426b4c2c/[email protected]" />
Detecting Microsoft Edge:
1//Extension ID: cnlefmmeadmemmdciolhbnfeacpdfbkd2<img src="chrome-extension://cnlefmmeadmemmdciolhbnfeacpdfbkd/src/images/eea2fd77fd2e973f20b26f45426b4c2c/[email protected]" />
Detecting Mozilla Firefox (ID can change at your Mozilla Firefox installation due to the randomized extension ID feature, but this actor can identify an incidence of Firefox browser just by defining an ELSE block after obtaining extension ID):
1// Extension ID: 910b3cf7-g3f2-3aa1-2211-21c313e00002<img src="moz-extension://910b3cf7-g3f2-3aa1-2211-21c313e0000/src/images/eea2fd77fd2e973f20b26f45426b4c2c/[email protected]" />
Further risks to privacy from extension detection
In addition to the risks regarding browser fingerprintability, the privacy effect can be much more devastating, as it can go as far as working out significant demographic information, from faith through to health issues or political leanings.
For example, according to academic research conducted in 2020 February by a group of Carnus researchers from University of Illinois at Chicago, “extensions can explicitly or implicitly disclose information that is personal (e.g., ethnicity) or sensitive (e.g., religion).”
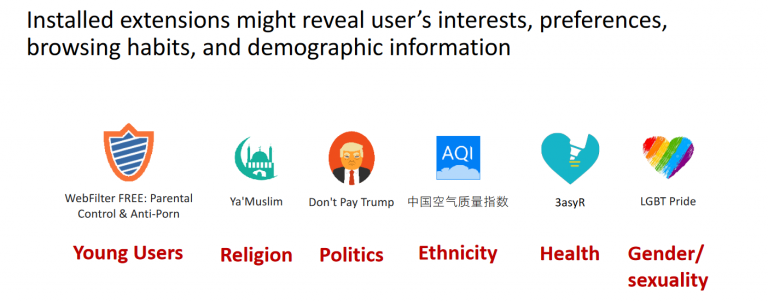 Of the Chrome Web Store's 29,428 fingerprintable extensions, analysis shows that at least 18,286 of them reveal this kind of demographic information. As for the more sensitive types of information? 116 extensions reveal a user's religious inclinations; 147, a user's medical or health conditions and 387 their political inclinations.
Of the Chrome Web Store's 29,428 fingerprintable extensions, analysis shows that at least 18,286 of them reveal this kind of demographic information. As for the more sensitive types of information? 116 extensions reveal a user's religious inclinations; 147, a user's medical or health conditions and 387 their political inclinations.
As the University of Illinois states:
"In the Health category we can find extensions such as UUID: knijgomkfcdigmbogcnffcbfgmapmkca, which is designed to assist people with dyslexia, and UUID: edmpbiamnlgdichailkadlagmbklhbpk, which allows users to compare their own images to visually similar skin cancer images on the web. In the Religion category there are extensions like UUID: ndmbeogingkjkmmkoomnigifmpajmbkc and UUID: apkkllhahggfkhfdlmpopcncnaiclfdm, which expose the user’s religion."
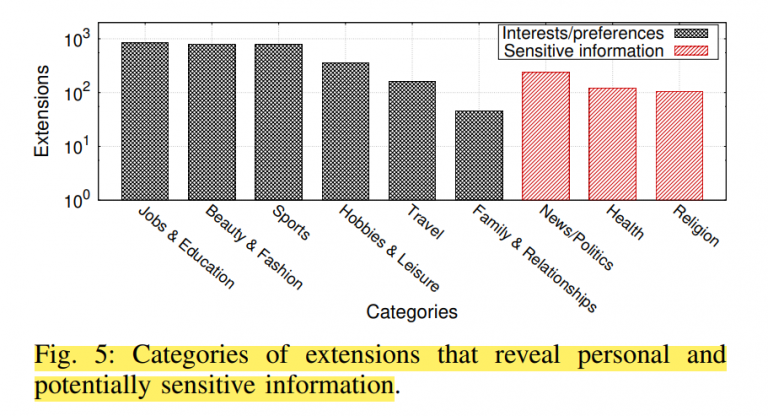 Extensions can be detected on a user's browser in just 10 seconds.
Extensions can be detected on a user's browser in just 10 seconds.
The unexpected dangers of reviews
Another unexpected area of risk crops up in reviews. As you know, to write a review of an extension, a user must first install that extension. By analyzing these reviews, it is possible to infer from which area mostly an extension is used, which language support the extension has, etc. It is also possible to reveal the user’s real name and profile picture if the user left a review for a fingerprintable extension.
It is possible to reveal a user's real name and profile picture if they left a review for a fingerprintable extension
Again, research backs this up.
“If an attacker detects 4 random extensions that are fingerprintable by our system, there is a 94.47% chance that she can uniquely identify the user and learn their name and profile picture. While this deanonymization attack is not applicable to all users, since not everyone writes reviews, it reveals a significant privacy risk that stems from a seemingly innocuous action, i.e., writing a review about a browser extension.”
Lulled into a false sense of security
You may be familiar with the idea of being lulled into a false sense of security, when you end up in a perception of a lower risk that doesn't match the reality. Take the example of someone using a VPN. They feel secure because they think they are hiding their location, but by also using a fingerprintable extension, that VPN becomes useless.
Many people prefer to use VPN not just to hide their real IP but bypass some regional restriction of contents by showing themselves as if they live in a different area than they do. Google Chrome Store supports 55 different languages in extensions, and it is undeniable that some extensions are mostly used by people from a specific region and people who speak a specific language. This helps in identifying users.
“(…)“FlashSaleTricks” extension (UUID: bboalniaekhennojedffbbjlokcpbjgn ) has a Shannon-Weiner index of 2.62. The language of that extension, and the text of its description, is English, but Indian names are predominant in its reviews. By checking its website, we found that it indeed targets Indian users. An interesting case is that of the “Download Master” (UUID: dljdacfojgikogldjffnkdcielnklkce), which appears to be popular among Russian users (SWI=3.47). While this extension is in English, we found that upon installation it downloads additional software that is in Russian. Similarly, while the description of the “J2TEAM Security” extension (UUID: hmlcjjclebjnfohgmgikjfnbmfkigocc) is in English, the majority of its reviewers are Vietnamese (SWI=3.21). In another example, the “wanteeed” extension (UUID: emnoomldgleagdjapdeckpmebokijail), with an index of 3.29, is shopping-related and is popular with French predominantly female users (2.9x more female names).”
How can you mitigate the risk of browser extension detection?
Both browser vendors and researchers have suggested and implemented some prevention mechanisms against browser extension fingerprinting. For example, in 2013, Google presented the second version of the manifest.json file that whitelists resources that can be used for web-accessible resources.
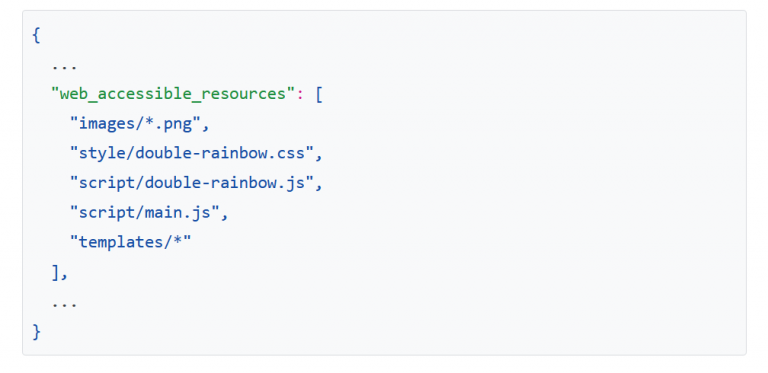 Firefox then applied randomized IDs for browser extensions generated browser instances, but rather than mitigating the issue, it allows adversaries to fingerprint users through web navigation, as we discussed in part one.
Firefox then applied randomized IDs for browser extensions generated browser instances, but rather than mitigating the issue, it allows adversaries to fingerprint users through web navigation, as we discussed in part one.
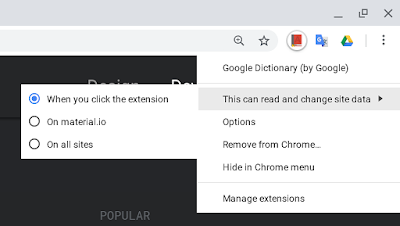 In 2018, Google Chrome offered host whitelisting per extension. With this feature, you can control the browser extension for the host on which it will be active or instruct the extension to be enabled after clicking the extension icon on the toolbar. As per their own explanation: “Beginning in Chrome 70, users will have the choice to restrict extension host access to a custom list of sites, or to configure extensions to require a click to gain access to the current page.” Please note that until this behavior is explicitly changed, an extension will behave as declared in the extension’s manifest.json file. However, this mitigation cannot protect your browser from extension detection attempts. It just protects the user from malicious extensions.
In 2018, Google Chrome offered host whitelisting per extension. With this feature, you can control the browser extension for the host on which it will be active or instruct the extension to be enabled after clicking the extension icon on the toolbar. As per their own explanation: “Beginning in Chrome 70, users will have the choice to restrict extension host access to a custom list of sites, or to configure extensions to require a click to gain access to the current page.” Please note that until this behavior is explicitly changed, an extension will behave as declared in the extension’s manifest.json file. However, this mitigation cannot protect your browser from extension detection attempts. It just protects the user from malicious extensions.
CloakX in 2019 by E. Trickel promises to prevent extension fingerprinting by randomizing WAR names and HTML elements added into the DOM by an extension. However, according to behavioral analyses of Carnus researchers, “Carnus will be able to uniquely identify 83.6-87.92% of the extensions that have behavioral fingerprints even if CloakX is deployed.”
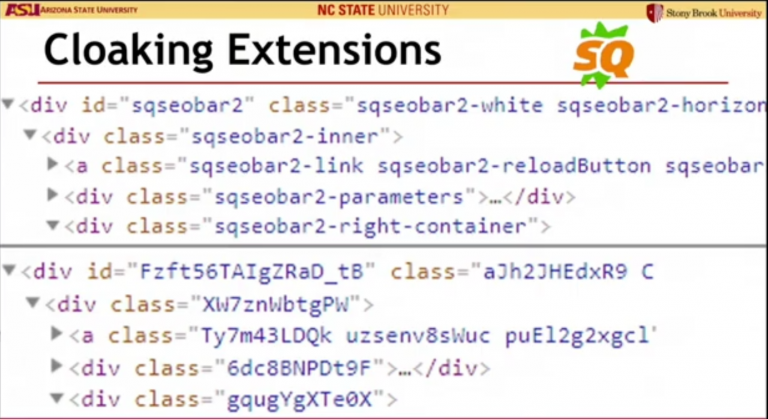 For Chromium-based browsers, there is no bulletproof solution to prevent extension detection completely. In addition to browser vendors, both extension developers and users can take responsibility jointly. For extension developers, they can avoid the use of web accessible resources as much as possible. If a developer needs to use some resources, developers should not modify the DOM in a predictable manner. Instead of a content script, developers may prefer to use browser or page action.
For Chromium-based browsers, there is no bulletproof solution to prevent extension detection completely. In addition to browser vendors, both extension developers and users can take responsibility jointly. For extension developers, they can avoid the use of web accessible resources as much as possible. If a developer needs to use some resources, developers should not modify the DOM in a predictable manner. Instead of a content script, developers may prefer to use browser or page action.
Likewise, users should also specifically pay attention to the extensions that promise fingerprint protection – and not let their guard down. Most of the time this kind of extensions alter DOM or browser object in a way that leaves tracks behind them as we already showed in the previous examples. Likewise, beware of lesser used extensions; as we said, most of the extensions in the market have less than 20 installs. Don’t prefer to use such extensions before being sure about all the fingerprint surface they reveal.
Importantly, Multilogin manages extensions for each browser profile separately and isolated for both Mimic and Stealthfox browsers. Our Firefox-based browser Stealthfox is also, as we have said before, free of the issue of fingerprintability due to randomized extension ID.
Multilogin manages extensions for each browser profiles separately with both Mimic and Stealthfox browsers. Stealthfox is also free of the issue of fingerprintability through randomized IDs.
Our research shows again the wide scope of the risks of browser fingerprinting, even in areas like supposedly anti-fingerprinting extensions. Make sure that you understand these risks and how they relate to a business dependent on maintaining multiple, separated accounts by keeping up to date with our blog.
[1] LinkedIn, Prohibited Software and Extensions, https://www.linkedin.com/help/linkedin/answer/56347/prohibited-software-and-extensions
[2] Prohitt, A Look at How LinkedIn Exfiltrates Extension Data from Their Users, https://prophitt.me/a-look-at-how-linkedin-exfiltrates-extension-data-from-their-users